Background?
Again, a different flavour of buffer overflows. String formatting functions can take a variable amount of parameters. EG: printf("Hey {0} {1}! Today is {2}...", arg_0, arg_1, ..., arg_n). The stack’s representation of that looks like this:
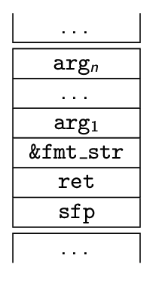
Ok… So how?
If an attacker is able to pass the actual string to be formatted, then the string format function is vulnerable. Using the code below, an adversary could print the next 4 values of the stack and then print the print the stack value as a pointer.
printf("%08x.%08x.%08x.%08x|%s");