What:
- They’re a tree-like data-structure used for Blockchain verification.
How:
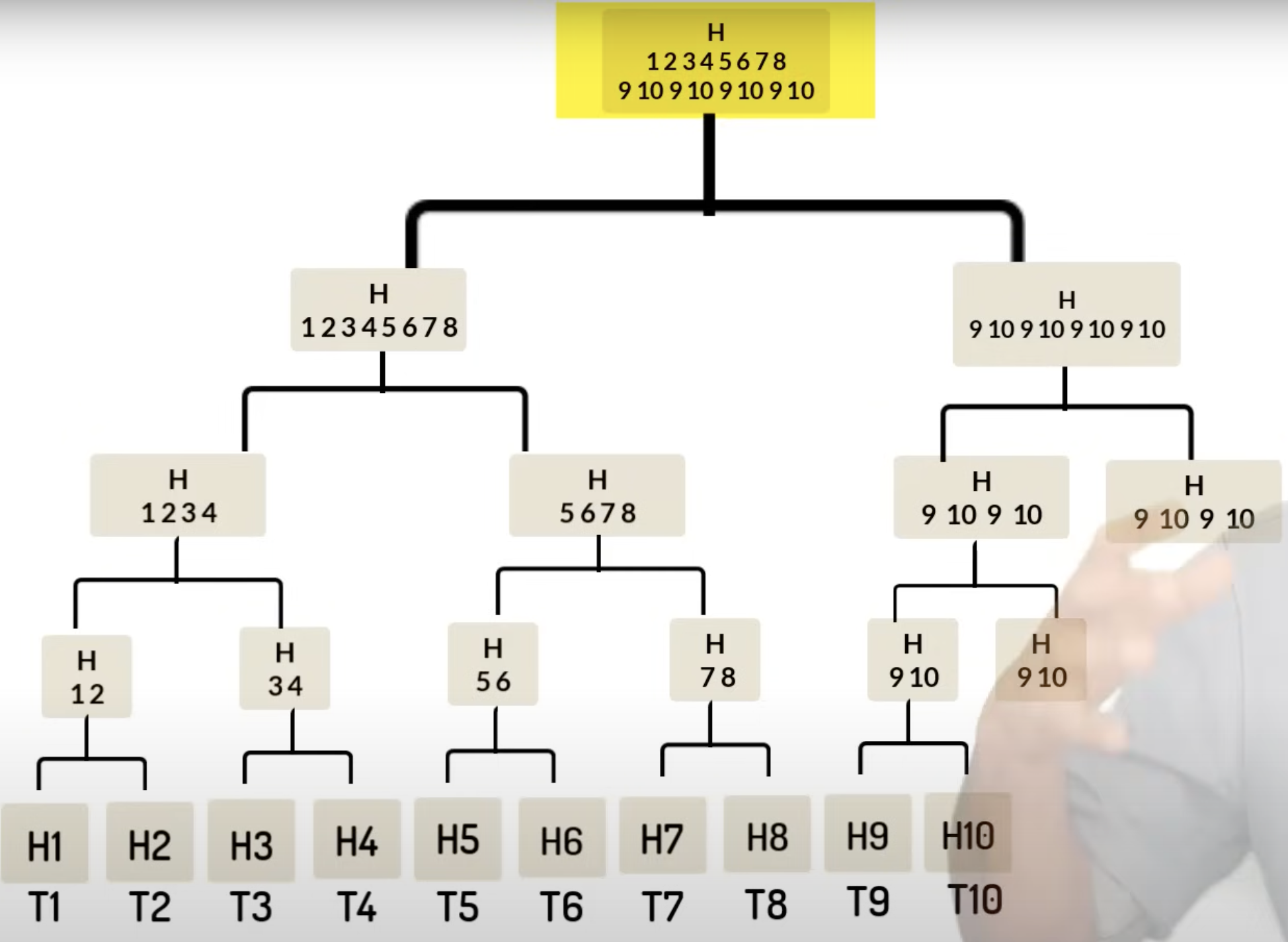
- Imagine you have a block of thousands of transactions.
- You hash them recursively in a tree manner, until you get a single hash for the root.
- If someone claims a hash belongs to that tree, they send it (and a few siblings) and you can compute their hashes. If the roots agree, then it does belong. (Proof Of Inclusion - without needing to download the entire tree).
Benefits:
- It’s logarithmic! O(log(n))