IP Vulnerabilities
When it comes to IPs, there’s lots of problems:
- No Source Authentication
- Sender that says “I’m
x, here’sy” could be an absolute lie lol.
- Sender that says “I’m
- No Integrity Checking
- All packets can be modified. Again, Man in the Middle attack applies here.
- No bandwidth constraints
- Denial of Service accounts because a source could flood all of that.
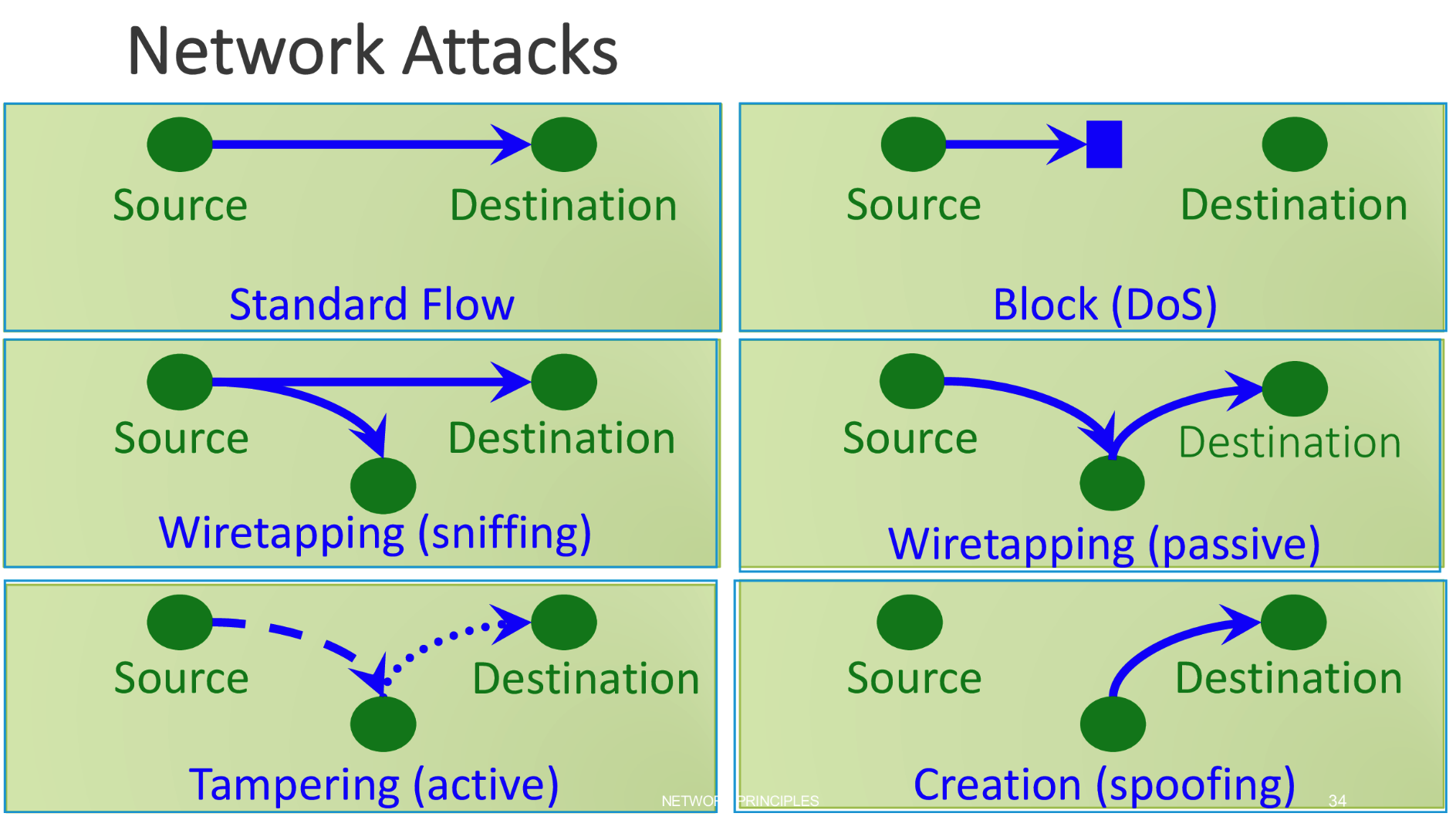
Some Network Attack Types include:
- DDOS
- Wiretapping / Sniffing
- Spoofing
- Tampering
Defences:
- Network Segmentation